Introduction to Binary Image Representation
Bit Planes form the fundamental building blocks of digital images by separating pixel intensity values into distinct binary layers. Moreover, understanding this concept unlocks deeper insights into how computers store, process, and manipulate visual information efficiently. Consequently, professionals in computer vision, graphics design, and data compression rely on these principles to optimize their work.
Understanding Digital Image Structure
Pixel Intensity and Binary Values
Digital images consist of countless pixels, each containing numeric values that represent color intensity or grayscale brightness levels. Furthermore, computers store these values using binary digits that range from simple black-and-white to millions of color variations. Therefore, converting human-perceivable images into machine-readable formats requires systematic organization of ones and zeros into meaningful patterns.
Gray Level Representation
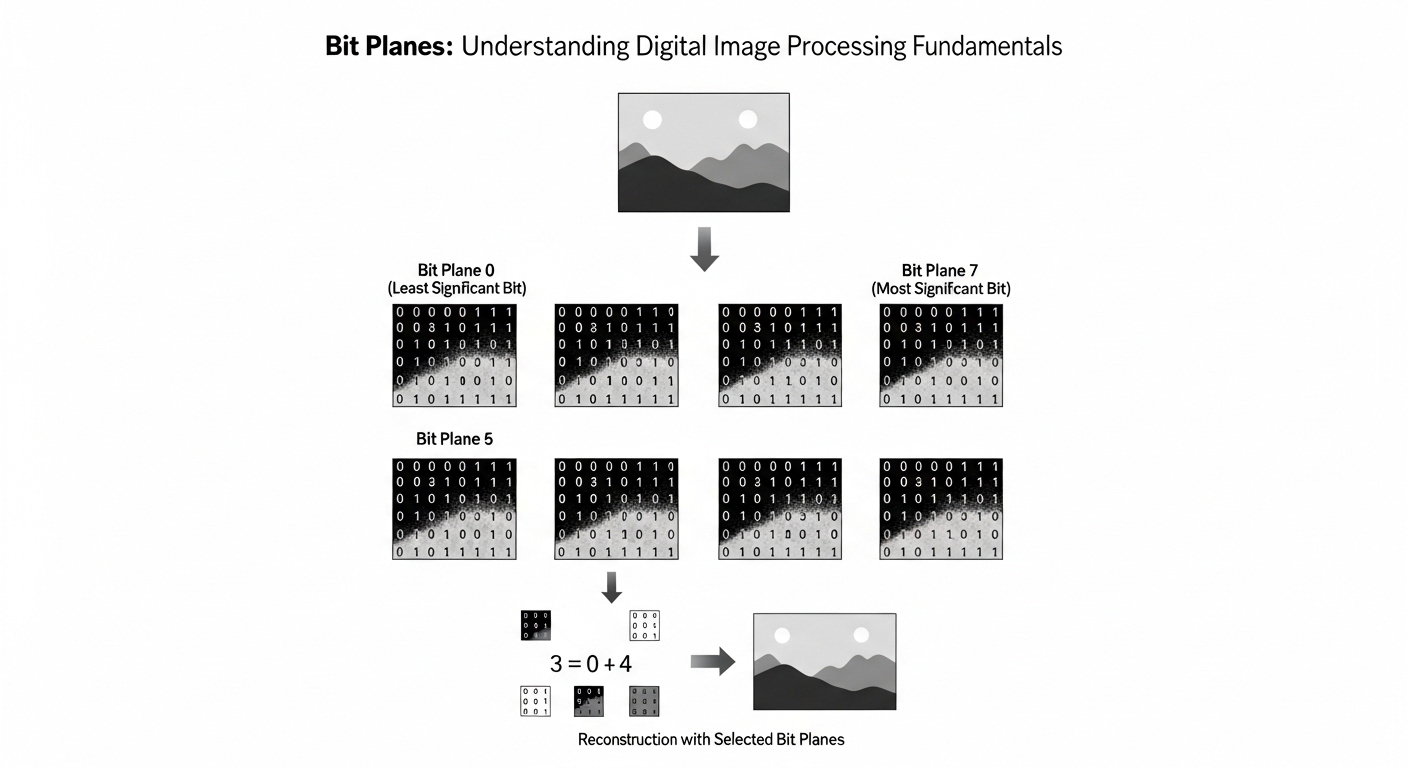
Grayscale images typically use eight bits per pixel, allowing 256 different intensity levels ranging from pure black to white. Additionally, each bit position contributes different weights to the final intensity value following powers of two in mathematics. The most significant bit carries weight 128, while the least significant bit contributes only one to total value.
Color Channel Components
Color images separate visual information into red, green, and blue channels, each containing its own intensity values independently. Meanwhile, combining these three primary color channels creates the full spectrum of colors humans perceive in natural scenes. Each channel operates using the same binary principles as grayscale images but contributes to final composite appearances differently.
Decomposing Images Into Binary Layers
The Decomposition Process
Image decomposition separates each pixel’s binary representation into individual layers where each layer corresponds to one bit position. Subsequently, this separation creates multiple binary images where pixels display either zero or one based on their original values. Eight-bit grayscale images produce eight separate layers, each revealing different information about the original image structure and content.
Most Significant Layers
Higher-order binary layers contain the most visually important information because they contribute greater weights to final pixel values. Moreover, these layers often reveal recognizable shapes, edges, and major features even when viewed independently without other layers. Consequently, preserving these layers becomes crucial when applying compression techniques that reduce file sizes by discarding less important data.
Least Significant Layers
Lower-order layers appear more random and noisy because they represent subtle intensity variations that human eyes struggle to perceive. Additionally, these layers often contain minor details, texture information, and sometimes embedded noise from image capture or processing. Therefore, many compression algorithms safely discard these layers without significantly affecting perceived image quality for most practical applications.
Applications in Image Processing
Lossless Compression Techniques
Understanding binary layer importance helps engineers design compression algorithms that preserve critical information while reducing storage requirements efficiently. Furthermore, separating significant data from redundant information allows systems to encode files more compactly without losing essential details. These techniques prove invaluable when archiving medical images, legal documents, or scientific data requiring perfect reproduction accuracy.
Lossy Compression Methods
Advanced compression schemes selectively discard less significant layers to achieve dramatic file size reductions while maintaining acceptable visual quality. Meanwhile, sophisticated algorithms analyze content and adaptively determine which layers viewers will unlikely notice when removed from final images. This approach enables streaming services, social media platforms, and web applications to deliver visual content faster over networks.
Image Enhancement Operations
Manipulating individual layers allows targeted adjustments that enhance specific image characteristics like contrast, sharpness, or noise reduction selectively. Additionally, filtering operations applied to separate layers can remove unwanted artifacts while preserving desirable features throughout the image. These techniques give photographers and graphic designers precise control over their creative vision and technical output quality.
Steganography and Data Hiding
Concealing Information Within Images
Lower significance layers provide ideal locations for embedding secret messages because modifications produce imperceptible changes to visual appearance. Moreover, this technique allows covert communication by hiding text, codes, or even entire files within innocent-looking photographs or graphics. Consequently, security professionals, journalists, and privacy advocates employ these methods for protecting sensitive information from unauthorized detection or interception.
Watermarking for Copyright Protection
Digital watermarks embedded in specific layers prove ownership and track unauthorized distribution of copyrighted images across internet platforms. Furthermore, these invisible markers survive common image manipulations like resizing, compression, or format conversion that pirates typically attempt. Therefore, content creators rely on watermarking technologies to protect intellectual property and monetize their creative work effectively.
Detection and Extraction Methods
Sophisticated analysis tools examine layer patterns to detect hidden data or verify watermark presence within suspicious or disputed images. Additionally, authorized parties use secret keys or algorithms to extract embedded information without damaging original image content permanently. These capabilities support forensic investigations, copyright enforcement, and secure communication channels in various professional contexts and applications.
Medical Imaging Applications
Diagnostic Image Analysis
Radiologists and medical imaging specialists analyze different layers to identify subtle abnormalities that might indicate diseases or injuries. Moreover, separating tissue density information into distinct layers helps distinguish between healthy and pathological structures more reliably than viewing. Consequently, early disease detection rates improve when specialists employ comprehensive layer analysis techniques during diagnostic examinations and screenings.
Image Quality Enhancement
Medical equipment manufacturers optimize imaging systems by understanding how noise and artifacts distribute across different significance layers. Subsequently, applying targeted noise reduction to lower layers while preserving diagnostic information in higher layers produces clearer images. These improvements enable more accurate diagnoses and reduce the need for repeat scans that expose patients to additional radiation.
Archival and Storage Solutions
Healthcare facilities manage massive image databases efficiently by compressing files using layer-based techniques that maintain diagnostic quality standards. Additionally, prioritizing critical layers ensures that compressed archives remain suitable for legal compliance and future medical reference needs. Therefore, hospitals save significant storage costs while meeting regulatory requirements for patient record retention and accessibility over time.
Computer Vision and Pattern Recognition
Feature Extraction Techniques
Machine learning algorithms analyze specific layers to identify edges, textures, and patterns that characterize objects within digital images. Furthermore, focusing on relevant layers reduces computational complexity and improves recognition accuracy by filtering out irrelevant noise and variations. These optimizations enable real-time processing in applications like facial recognition, autonomous vehicles, and industrial quality control systems.
Object Detection Systems
Automated systems examine layer combinations to locate and classify objects within complex scenes containing multiple overlapping elements and backgrounds. Meanwhile, different object types often produce distinctive patterns across various significance levels that trained algorithms learn to recognize reliably. Consequently, security cameras, robotics, and augmented reality applications achieve impressive performance using these sophisticated analytical approaches consistently.
Image Segmentation Methods
Separating images into meaningful regions becomes more effective when algorithms consider how boundaries and textures manifest across different layers. Additionally, combining information from multiple layers creates robust segmentation that handles challenging conditions like poor lighting or low contrast. These capabilities prove essential for medical imaging, satellite analysis, and document processing applications requiring precise region identification.
Cryptography and Security
Encryption Through Layer Manipulation
Scrambling specific layers using cryptographic keys renders images unrecognizable without proper decryption algorithms and authorized access credentials. Moreover, this approach allows selective encryption where sensitive portions receive protection while leaving other areas viewable for indexing purposes. Therefore, government agencies, financial institutions, and healthcare organizations employ these techniques to secure confidential visual data against breaches.
Authentication and Verification
Embedded authentication codes within specific layers enable systems to verify image integrity and detect unauthorized modifications or tampering attempts. Furthermore, comparing layer characteristics between original and questioned images reveals even subtle alterations that simple visual inspection misses. These verification methods support legal proceedings, journalism ethics, and scientific research integrity by ensuring photographic evidence remains authentic.
Secure Communication Channels
Combining encryption and steganography creates covert communication systems that hide both message existence and content from surveillance efforts. Additionally, transmitting secret information through innocuous images attracts less attention than obviously encrypted files that trigger security monitoring. Consequently, activists, journalists, and intelligence agencies utilize these dual-protection methods when operating in hostile or monitored environments.
Educational and Research Implications
Teaching Digital Concepts
Educators use binary layer visualization to help students understand abstract digital representation concepts through concrete, observable visual examples. Moreover, interactive demonstrations allow learners to manipulate individual layers and observe effects on final images in real time. Therefore, these hands-on experiences build stronger intuitive understanding than purely theoretical explanations of binary encoding and digital processing.
Research Tool Development
Scientists develop novel analysis techniques by exploring how different phenomena manifest across various significance levels in experimental imaging. Additionally, interdisciplinary collaborations between computer scientists and domain experts reveal new applications and insights previously unconsidered by either field. These innovations advance both theoretical understanding and practical capabilities across numerous scientific and engineering disciplines continuously.
Innovation and Future Directions
Emerging technologies like quantum computing and artificial intelligence promise revolutionary advances in how we process and analyze layered data. Furthermore, new display technologies might eventually render images by directly manipulating individual layers rather than final composite values. Therefore, continued research into fundamental concepts remains essential for enabling breakthrough applications that transform digital imaging capabilities dramatically.
Practical Implementation Considerations
Programming and Algorithm Design
Software developers implement layer decomposition using bitwise operations that efficiently extract individual bits from multi-bit pixel values programmatically. Meanwhile, modern programming languages provide built-in functions and libraries that simplify these operations for developers without deep mathematical backgrounds. Consequently, implementing sophisticated image processing applications becomes accessible to broader developer communities than ever before in technology history.
Performance Optimization Strategies
Processing individual layers sequentially rather than entire images simultaneously often improves computational efficiency and reduces memory requirements significantly. Additionally, parallel processing techniques allow simultaneous layer manipulation across multiple processor cores or specialized graphics processing units effectively. These optimizations enable real-time processing of high-resolution video streams that would otherwise overwhelm conventional computing architectures and systems.
Hardware Acceleration Options
Specialized processors designed for image processing execute layer operations much faster than general-purpose CPUs through dedicated circuit architectures. Furthermore, field-programmable gate arrays allow customization for specific applications requiring maximum performance and energy efficiency simultaneously. Therefore, choosing appropriate hardware becomes crucial when developing commercial products or research systems with demanding performance requirements.
Conclusion: Foundation for Digital Innovation
Binary layer concepts provide essential foundations for understanding and advancing digital image technology across countless applications and industries. Ultimately, mastering these fundamental principles empowers professionals to create innovative solutions that push technological boundaries and solve real-world problems. Continue exploring these concepts to unlock new possibilities in your own work and contribute to ongoing digital revolution.